Integrate and Automate
Send and receive Threema messages with your own software. More secure, affordable, and versatile than SMS.
Send and receive Threema messages with your own software. More secure, affordable, and versatile than SMS.

Threema Gateway’s use cases are virtually unlimited. Here are some examples of how Threema can be integrated into third-party systems.
Use Threema for two-factor authentication.
Create your own Threema bot or Threema service (example: Corona Radar).
Integrate Threema into your existing process automation solution (example: TK Elevator).
Monitor systems and automatically send a Threema message in case of emergencies or specific queries (example: Open Circle AG, Wazuh).
Monitor a website and receive a Threema message when a change occurs, sent to the pre-defined Threema ID.
Threema Gateway works just like an SMS gateway, but it’s more versatile. At the center of the service lies the Threema Gateway server, which processes incoming messages and forwards the information to the desired Threema users, user groups, or systems.
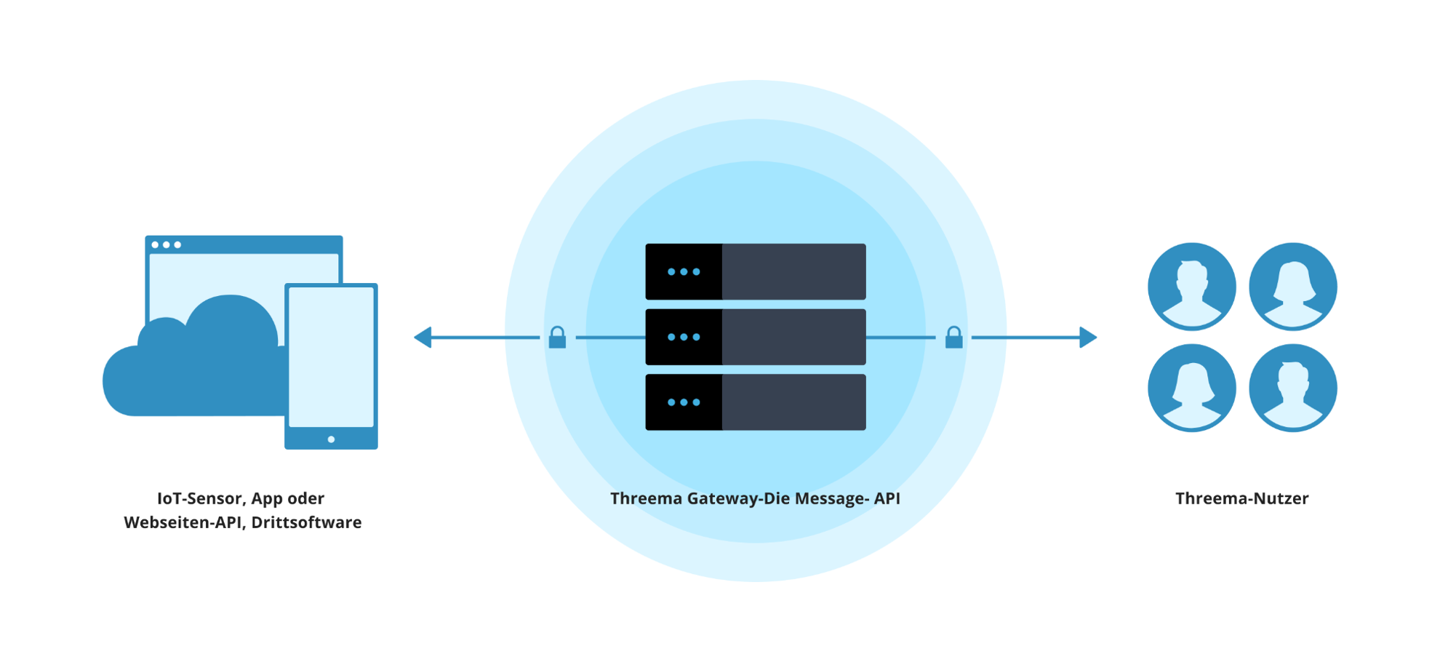
Asymmetric cryptography guarantees that only the intended recipient can read your messages.
The encryption in Threema is verifiable. You encrypt the messages directly on your server using open source software.
Sign up for free, no recurring fees. Send a message already from CHF 0.01.
Threema messages can be received without mobile network coverage as long as there is a working Internet connection.
Send and receive text messages (up to 3,500 characters), images, and files of any type.
Ensure recognition value by requesting a custom ID and a custom profile picture. Example ID: *THREEMA
Learn more about Threema Gateway’s features in the API documentation.
Threema Gateway lets you request your personal, custom ID. All IDs that are used on Threema Gateway start with an asterisk (*) and consist of 8 characters in total. Example ID: *ALERT4U. You can also personalize your custom ID by setting a profile picture.
The Threema app displays Gateway contacts with a generic business icon and a custom profile picture.
Incident Management (CDC)
In the video, Tom F. Hofmann, CISO and founder of wicked.design GmbH, explains how they integrate Threema into their Cyber Defence Center. Connecting Threema to the security platform Wazuh enables targeted information and alerting from secure configuration management, file and cloud monitoring, threat intelligence, and malware detection.