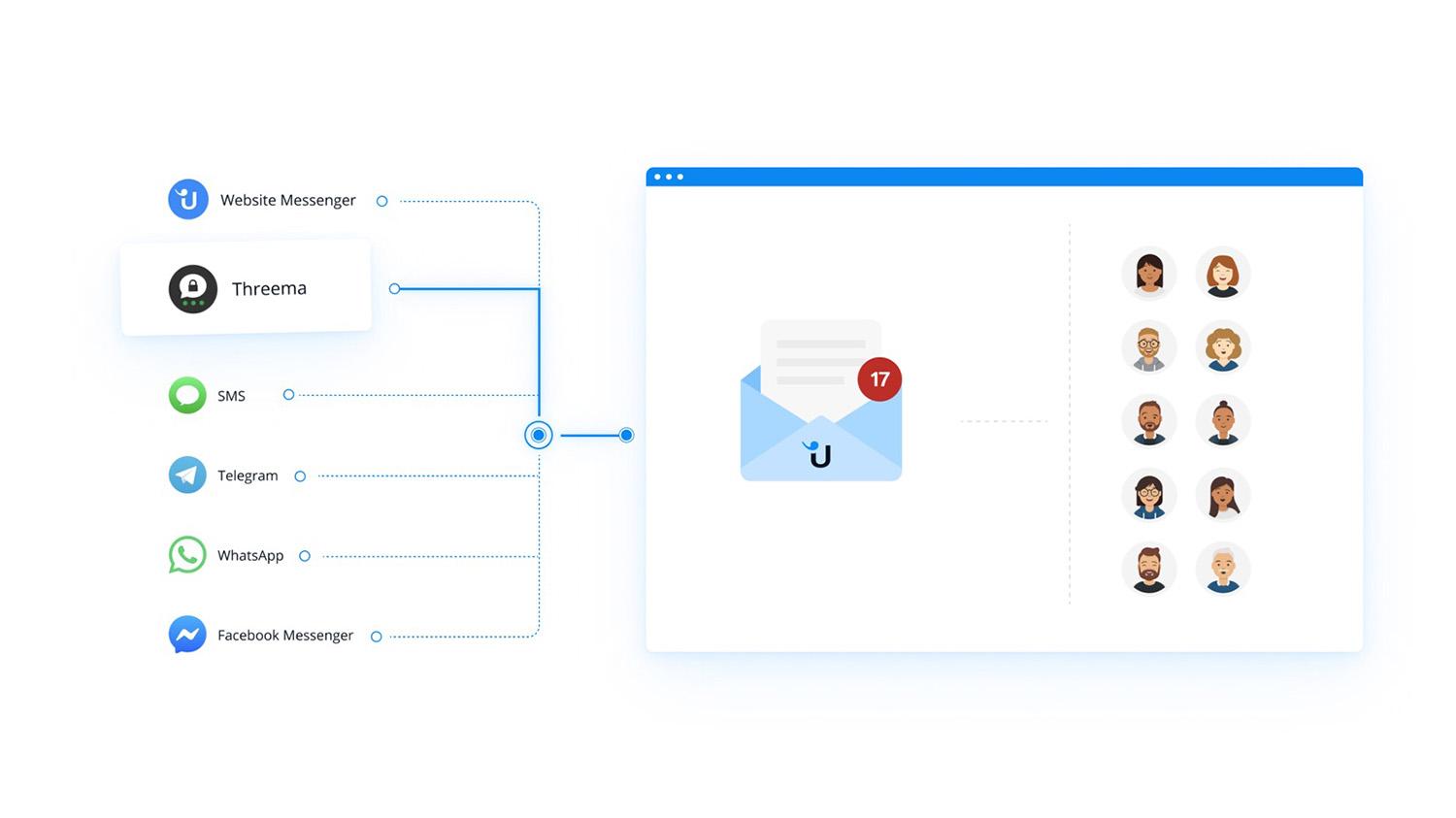
Threema and Userlike: Facilitate Team and Customer Communication
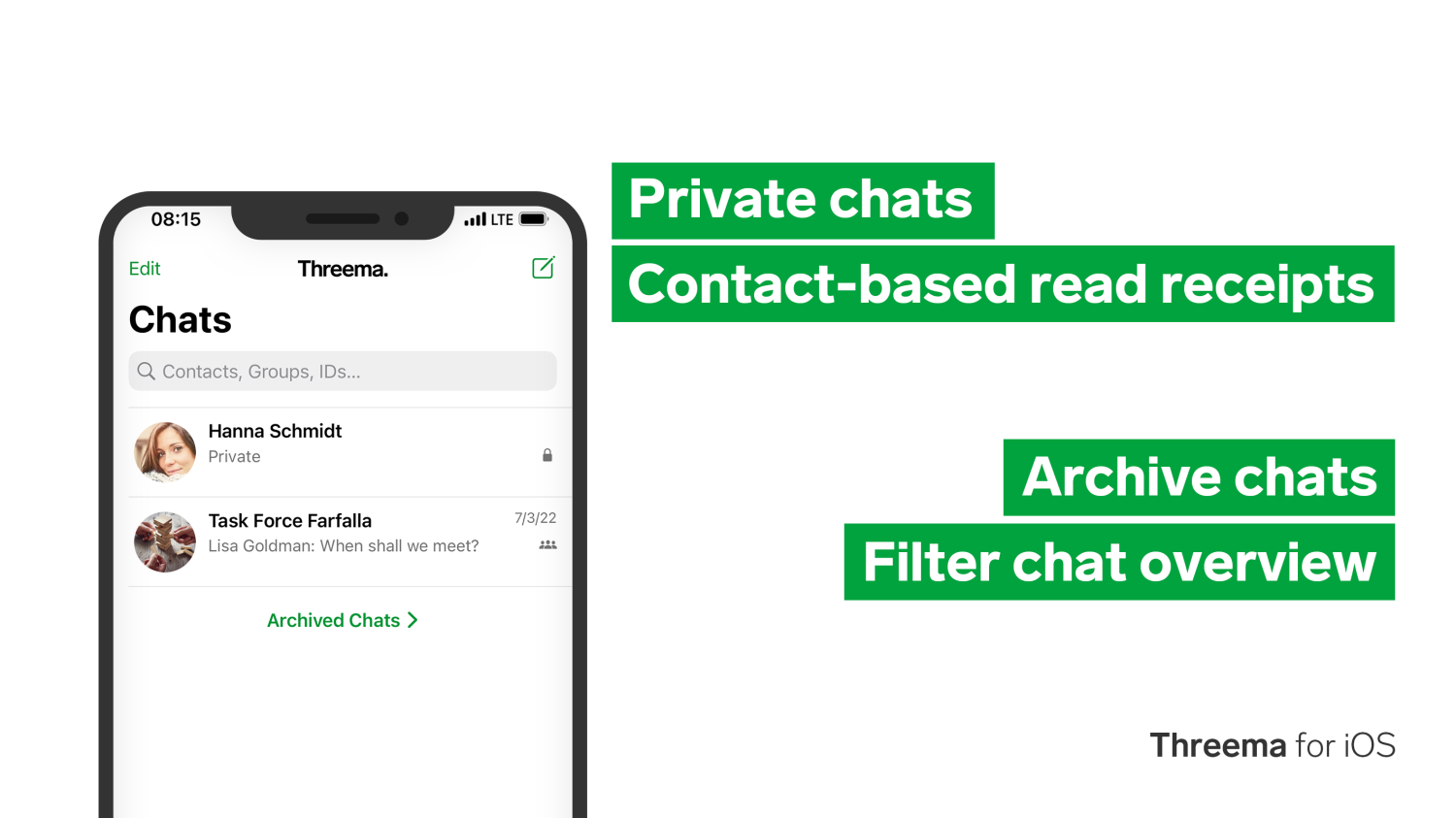
Would you like to offer your employees and customers a secure channel to contact you? Or do you need a fast and efficient way to process help-desk tickets? Exchange messages securely with Threema and let your team answer tickets directly from a shared inbox with the Userlike software.