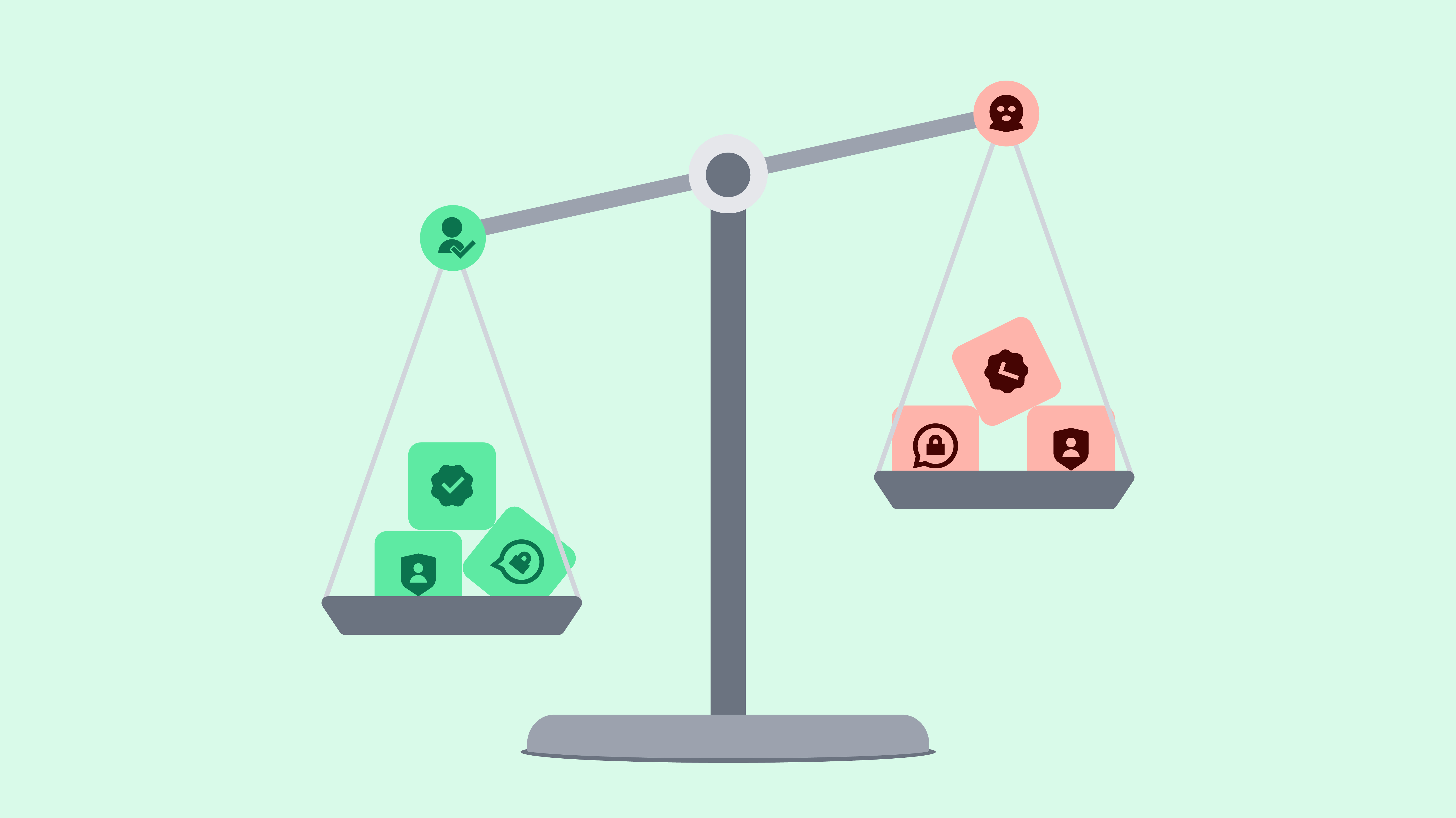
Privacy for Everyone vs. Mass Surveillance for Crime Prevention
Have you ever heard the phrase “I have nothing to hide”? It’s often used by people who advocate government surveillance as a means of combating crime. According to this logic, however, anyone who is not a criminal has nothing to hide and therefore does not need an encrypted communication channel. This assumption is not only wrong, but also quite dangerous.