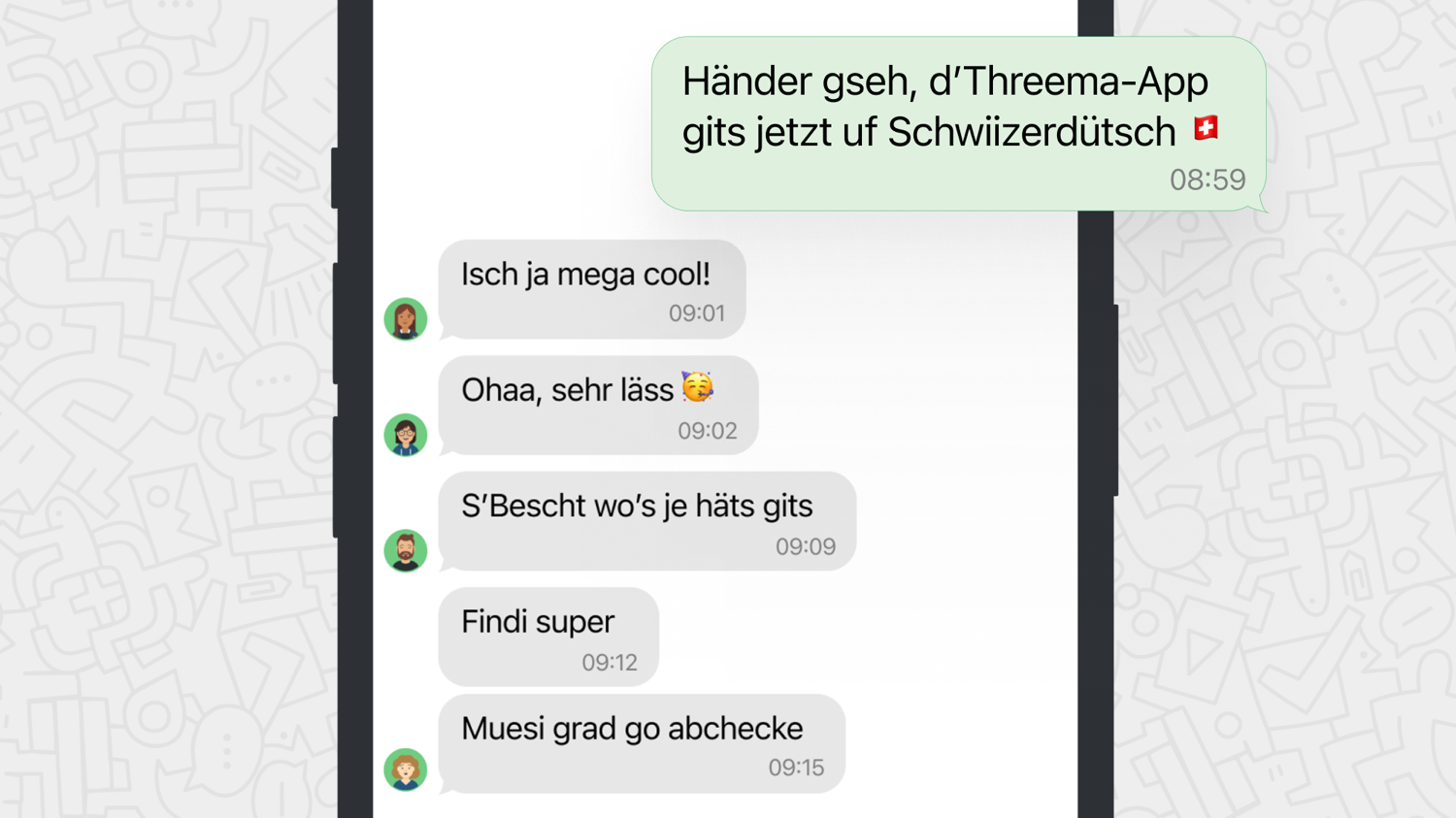
Threema Is Now Available in Swiss German
For the longest time, Swiss German was exclusively a spoken language – everything written had to be in standard German. This has changed with the emergence of chat apps like Threema: with its informal character, instant messaging helped dialects find their way into written communication.